Management Interface Selection for Network Devices
In this chapter, you’ll learn how Nectus selects Management Interfaces for Devices that are found during Discovery phase. Nectus will automatically select Management Interfaces using its own default logic. It also supports user-defined selection for cases where this is appropriate.
The specific topics we will cover in this chapter are:
- Default Logic for Management Interface Selection
- User-Defined Logic for Management Interface Selection
- Applying Selection Rules to Existing Devices
1. Default Logic for Management Interface Selection
During Discovery, Nectus finds all SNMP Devices on the network. Every Device has one or more Interfaces. Some of those Interfaces will have IP Addresses assigned to them, and could be used as the Management Interface for that Device.
Nectus has default logic for selecting the Management Interface for each Device. It checks every Interface on a Device looking for potential Management Interfaces. To be considered for selection as the Management Interface, an Interface must meet the following requirements:
- It must have a unique IP Address. Nectus will not select an Interface that does not have an IP Address, or that has an IP Address identical to some other Interface on the network.
- It must be Up. Netus will not select an Interface that is not Up.
From this list of possible Management Interfaces, Nectus selects one according to this priority list:
- An Interface name that begins with Mgmt
- An Interface name that begins with Loopback
- An Interface name that begins with Vlan
- Interface with lowest IP Address
If Nectus finds an Interface name that begins with Mgmt, it will use this as the Management Interface. If it does not find an Interface name that begins with Mgmt, it will look for one that begins with Loopback, and so on.
If Nectus does not find an Interface whose name starts with Mgmt, Loopback, or Vlan, it will select the lowest numbered IP Address on the Device.
This default logic allows Nectus to automatically select the correct Management Interface in most situations. To handle situations where the default logic is not appropriate, Nectus supports user-defined logic for Management Interface selection.
2. User-Defined Logic for Management Interface Selection
Defining your own Management Interface selection logic makes sense in two situations:
- When the naming convention for your Interfaces doesn’t match the default rules
- When specific Interfaces have special naming requirements
When a Device has applicable user-defined Management Interface selection logic, Nectus looks for that Interface before applying the default logic. As with the default logic, user-defined Management Interfaces:
- Must have a unique IP Address.
- Must be Up.
To create user-defined logic for a specific Device type right-click the Device name. In the menu that appears, select View Device Info.
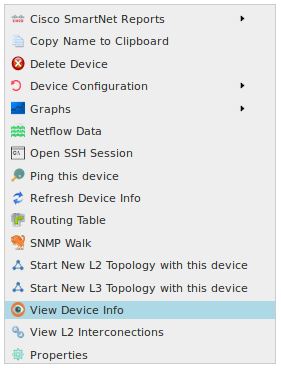
This opens the “View Device Info” dialog box.
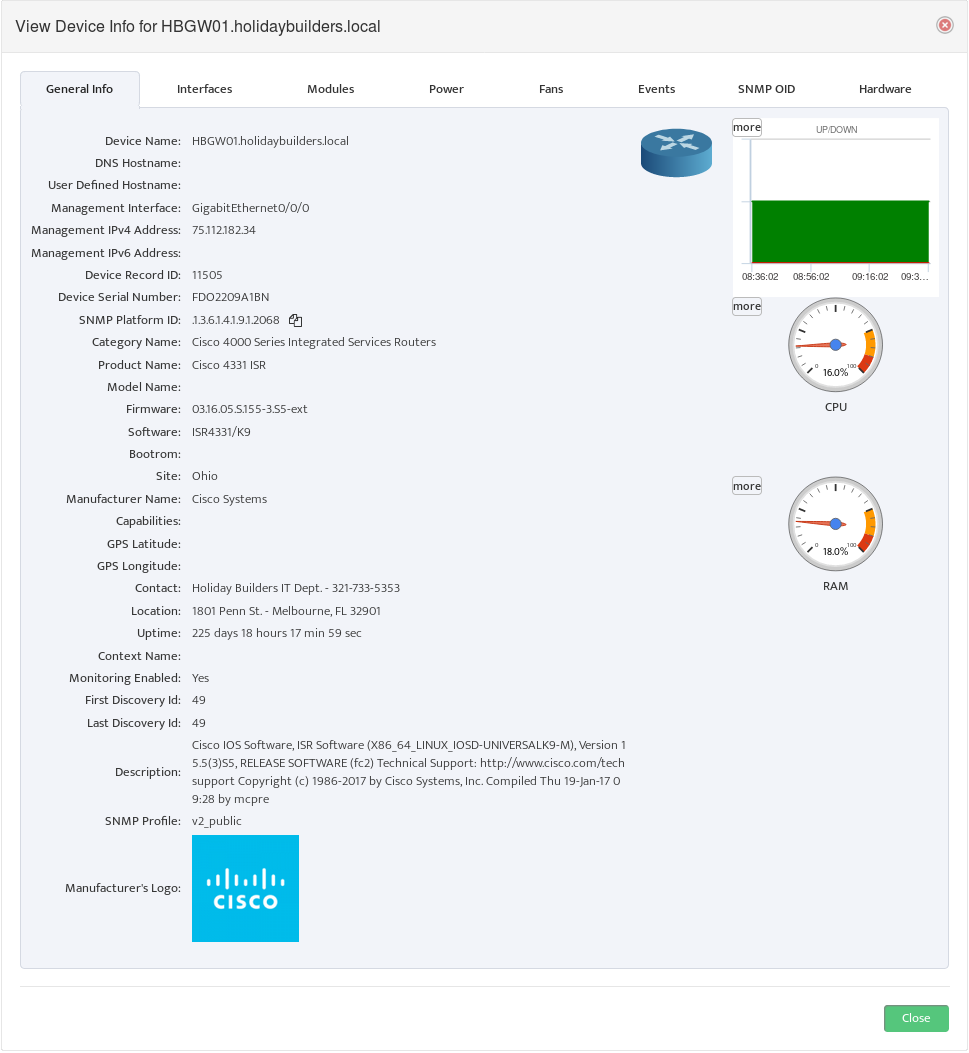
On the General Info tab, find the SNMP Platform ID and click the icon to the right of it to copy the ID.
Note: All Devices with the same model number have the same SNMP Platform ID.
Next Step is to go to Settings -> Products and Categories -> SNMP OID Libraries.
Select SNMP OID Libraries.
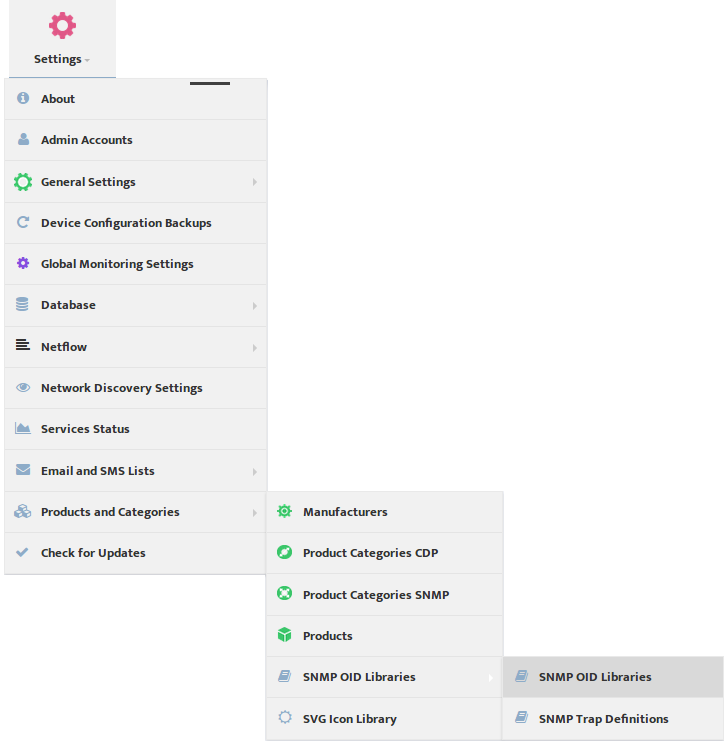
This opens the “SNMP OID Libraries” dialog box.
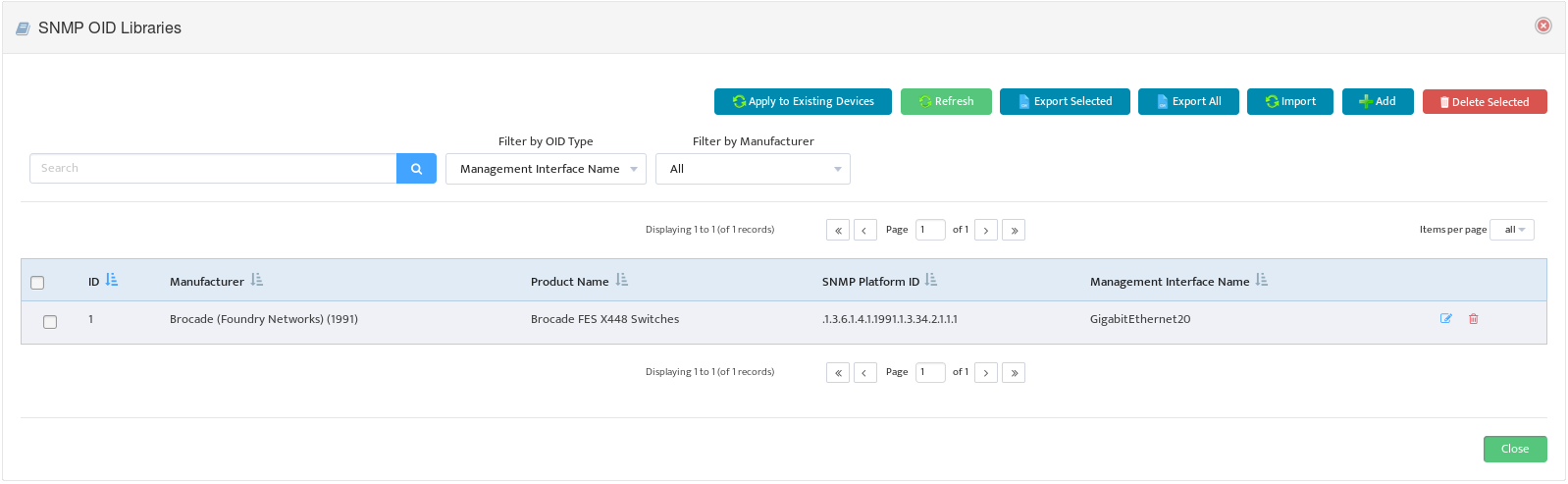
Select Management Interface Name in the Filter by OID Type list. Nectus displays all the current user-defined Management Interface Selection rules.
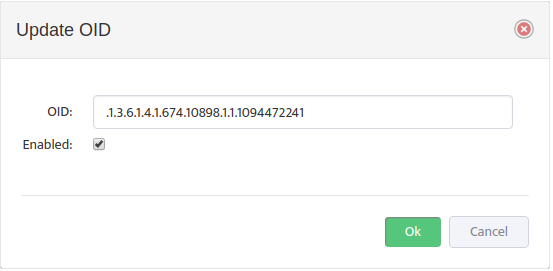
Click the Add button to open the “Add” dialog box.
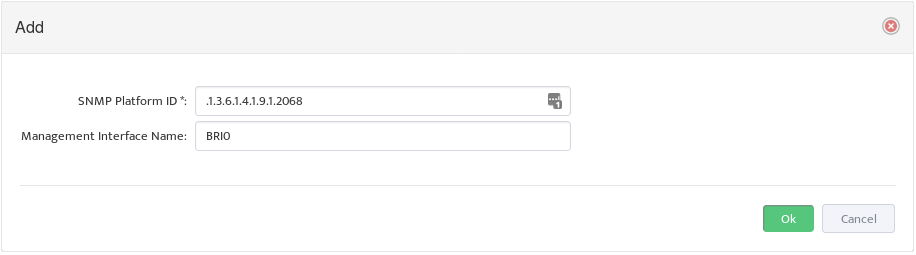
Enter the SNMP Platform ID and the Management Interface Name Nectus should use for this type of Device.
3. Applying Selection Rules to Existing Devices
Defining new Management Interface selection rules will have automatic effect on all devices that will be discovered after rule is created but does not automatically apply those rules to existing Devices.
You need to tell Nectus to apply those changes to existing Devices.
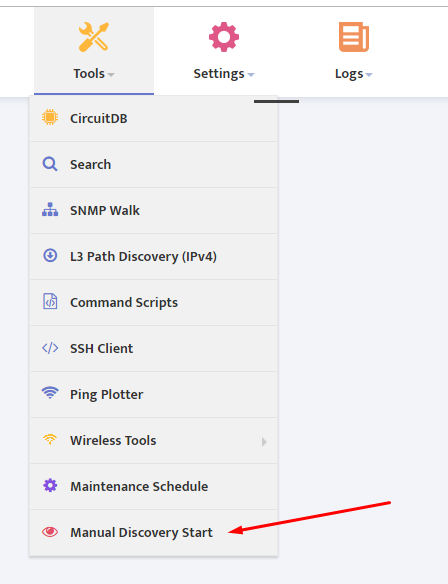
To apply the user-defined selection rules to existing Devices, return to the “SNMP OID Libraries” dialog box and click the “Apply to Existing Devices” button.

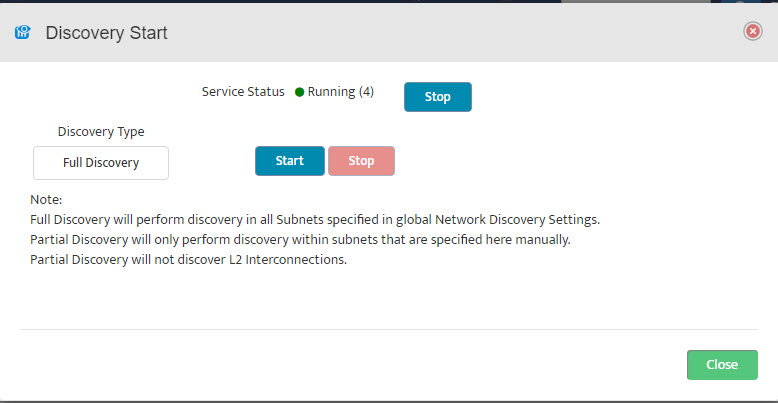
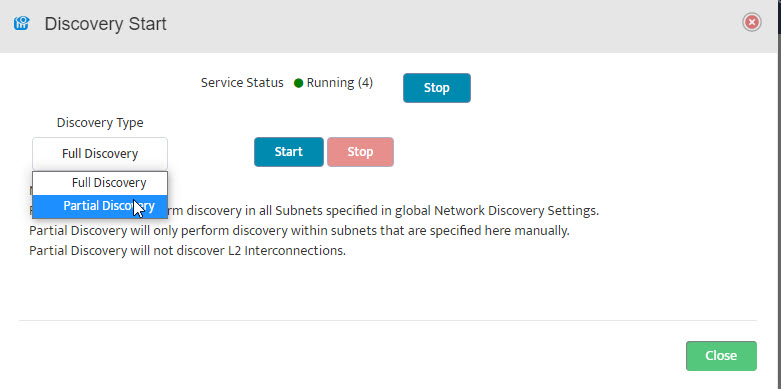
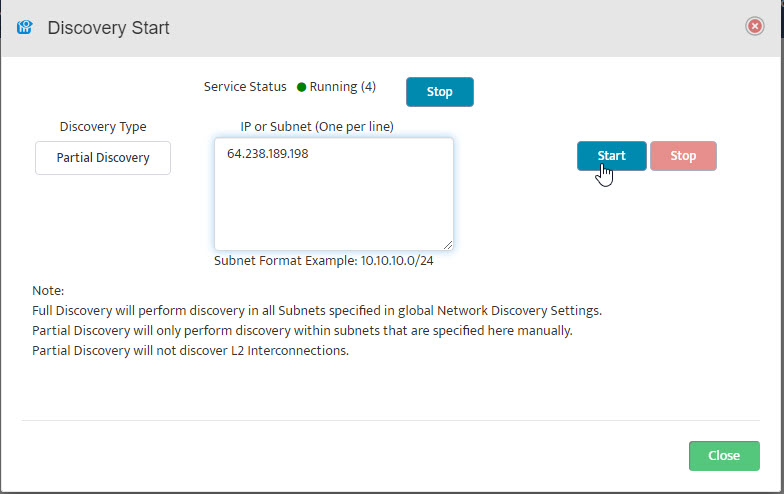
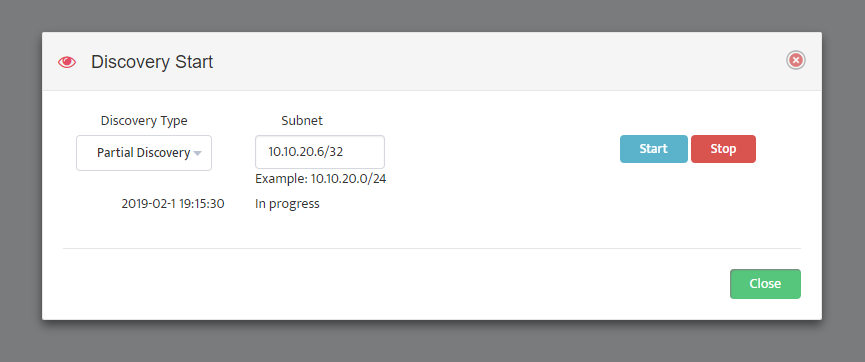
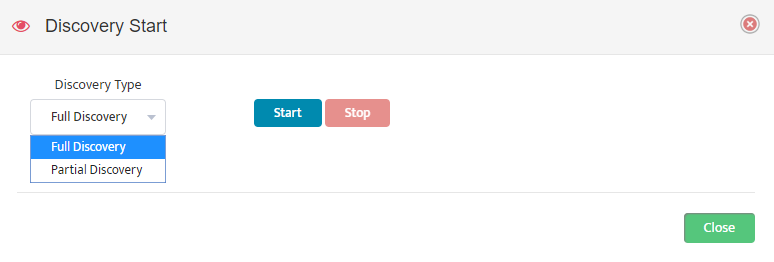
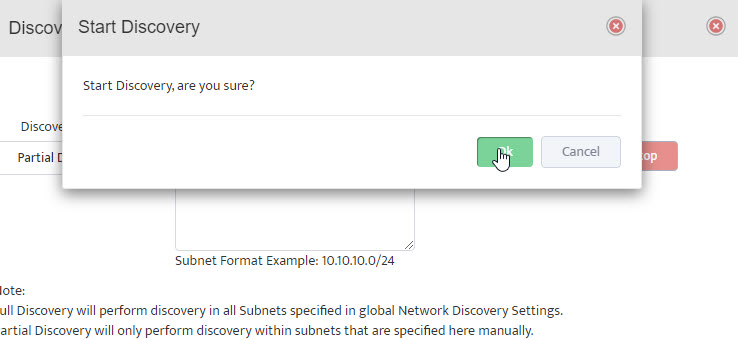 The Start Discovery window asks, “Start Discovery, are you sure?” Click “OK”.
The Start Discovery window asks, “Start Discovery, are you sure?” Click “OK”.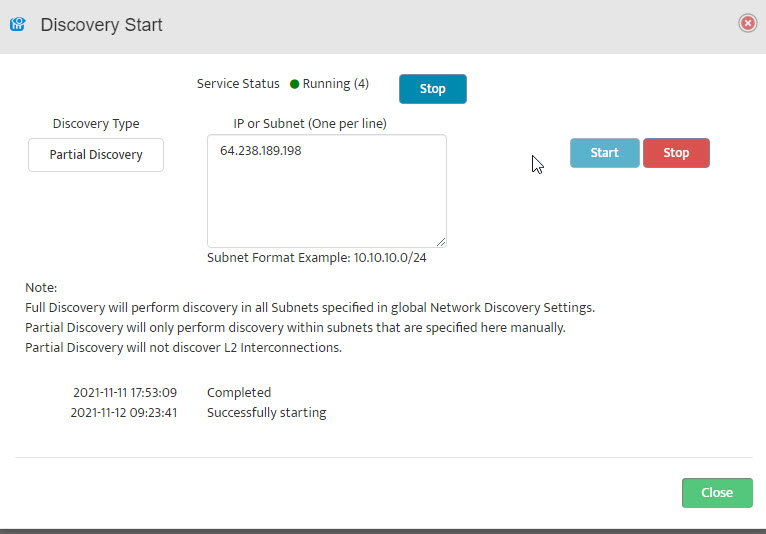 Close the Discovery Start window by clicking on “Close” in the lower right-hand side.
Close the Discovery Start window by clicking on “Close” in the lower right-hand side.
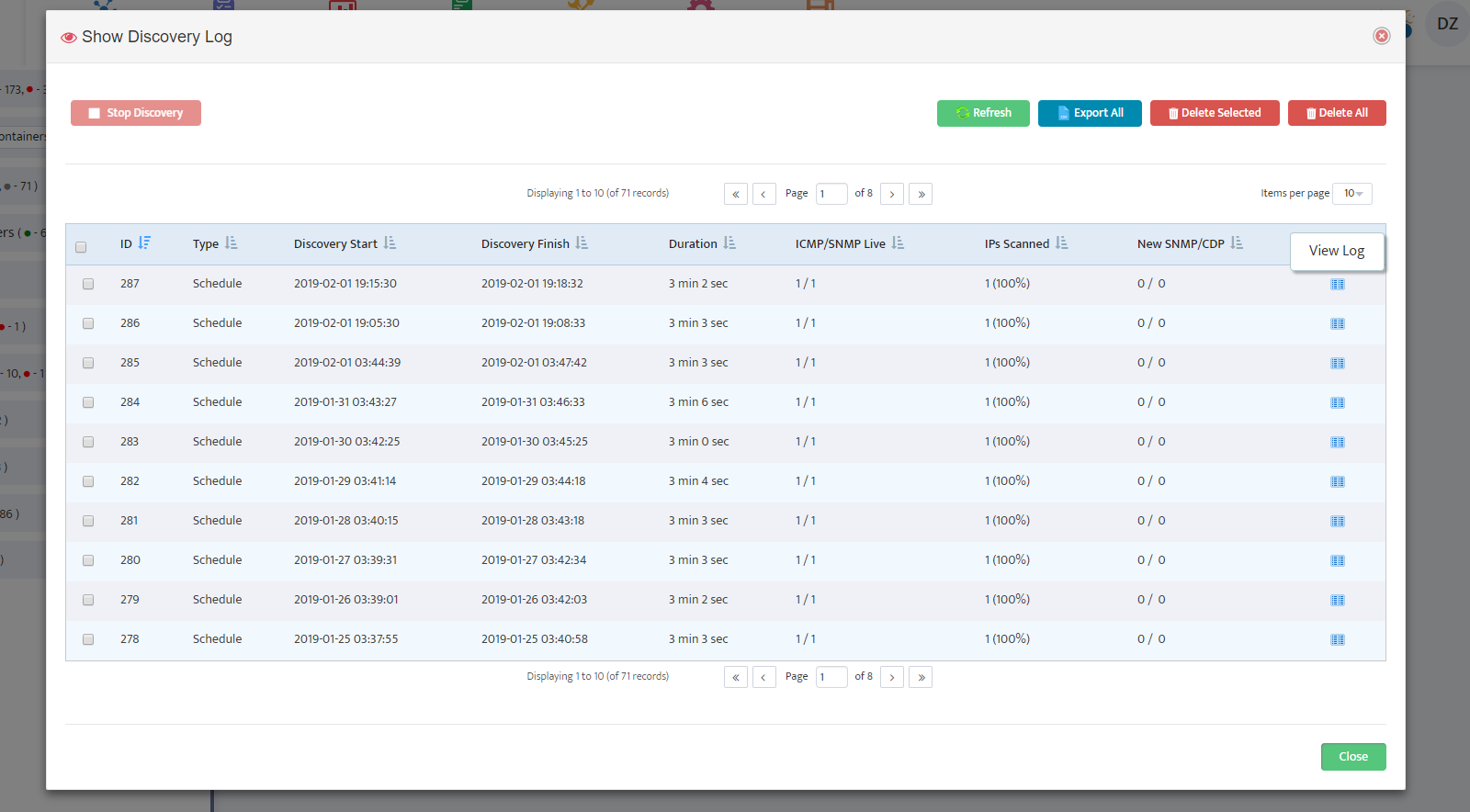
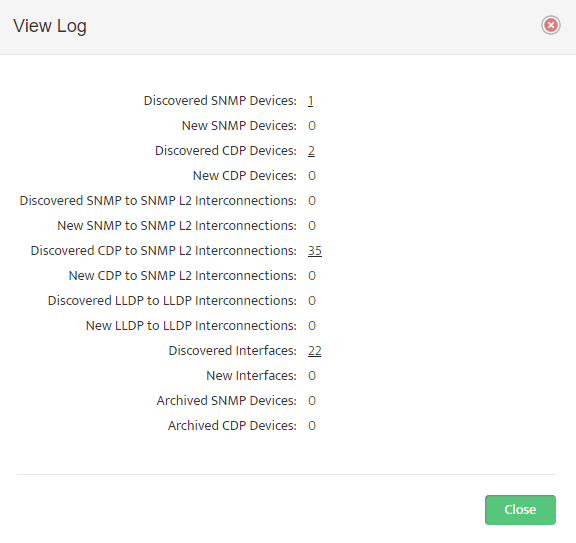
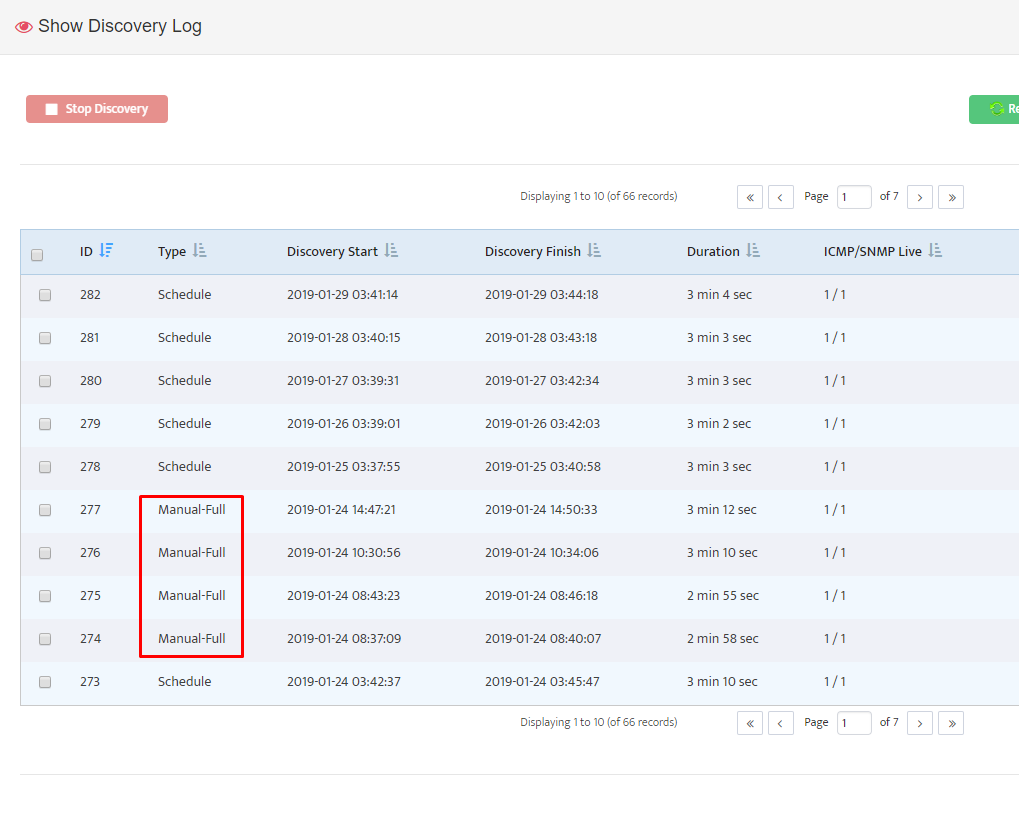
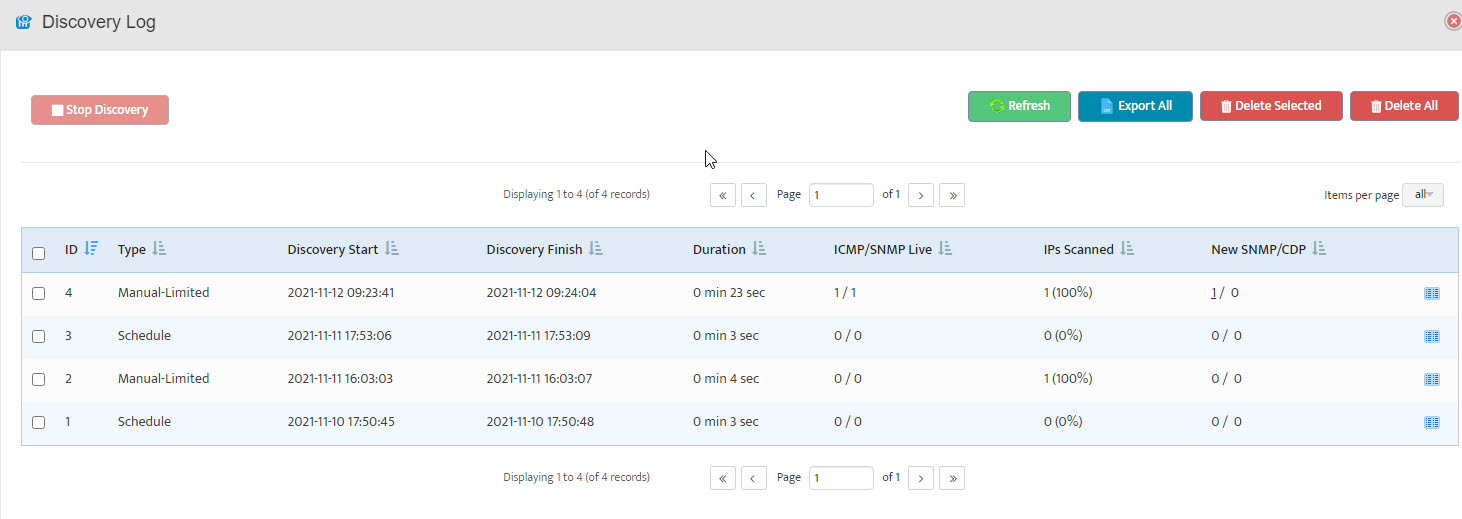 The Discovery Log opens. Here we see that our discovery (ID 4) ran to completion in 0 minutes and 23 seconds.
The Discovery Log opens. Here we see that our discovery (ID 4) ran to completion in 0 minutes and 23 seconds.